 |

15
Protected
Mode
Programming
15.1.
INTRODUCTION
Till
now we have been discussing
the 8088 architecture which was a
16bit
processor.
Newer processors of the
Intel series provide 32bit
architecture. Till
now we
were in real mode of a newer
processor which is basically a
compatibility
mode making the newer
processor just a faster
version of the
original
8088. Switching processor in
the newer 32bit mode is a
very easy
task.
Just turn on the least significant bit of
a new register called
CR0
(Control
Register 0) and the
processor switches into
32bit mode called
protected
mode. However manipulations in
the protected mode are
very
different
from those in the read
mode.
All
registers in 386 have been
extended to 32bits. The new
names are EAX,
EBX, ECX, EDX,
ESI, EDI, ESP, EBP, EIP,
and EFLAGS. The original
names
refer
to the lower 16bits of these
registers. A 32bit address
register can
access
upto 4GB of memory so memory
access has increased a
lot.
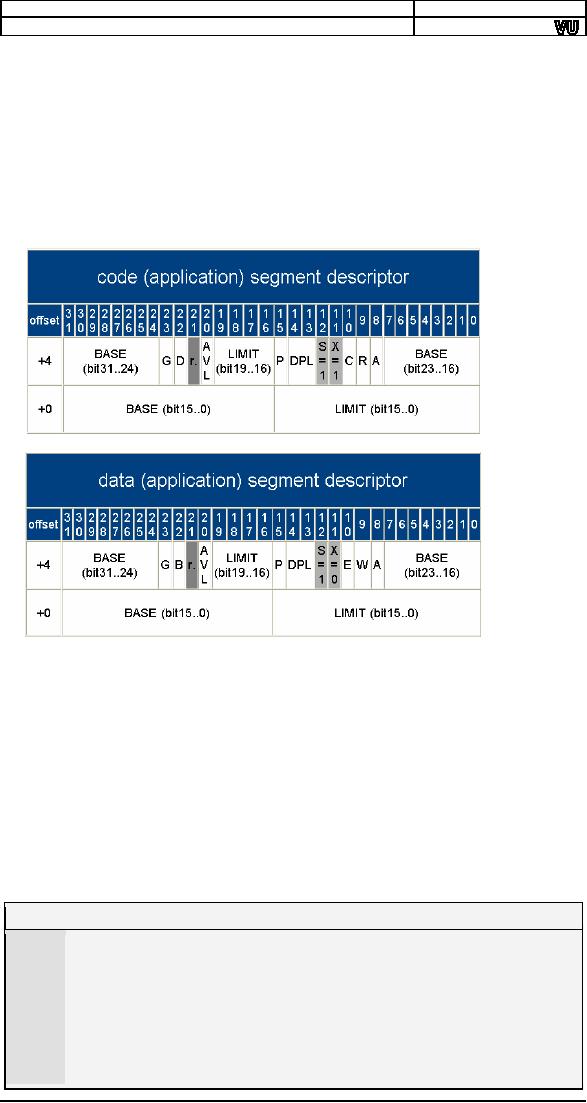
As
regards segment registers
the scheme is not so simple.
First of all we
call
them segment selectors instead of
segment registers and they
are still
16bits
wide. We are also given two
other segment selectors FS
and GS for no
specific
purpose just like
ES.
The
working of segment registers as
being multiplied by 10 and
added into
the
offset for obtaining the
physical address is totally
changed. Now the
selector
is just an index into an
array of segment descriptors
where each
descriptor
describes the base, limit,
and attributes of a segment.
Role of
selector
is to select on descriptor from
the table of descriptors and
the role of
descriptor
is to define the actual base
address. This decouples the
selection
and
actual definition which is needed in
certain protection
mechanisms
introduced
into this processor. For
example an operating system
can define
the
possible descriptors for a
program and the program is
bound to select
one of
them and nothing else. This
sentence also hints that
the processor
has
some sense of programs that
can or cannot do certain
things like change
this
table of descriptors. This is
called the privilege level
of the program and
varies
for 0 (highest privilege) to 3
(lowest privilege). The
format of a selector
is
shown below.
The
table index (TI) is set to 0
to access the global table
of descriptors
called
the GDT (Global Descriptor
Table). It is set to 1 to access
another
table,
the local descriptor table
(LDT) that we will not be
using. RPL is the
requested
privilege level that ranges
from 0-3 and informs what
privilege level
Computer
Architecture & Assembly Language
Programming
Course
Code: CS401
CS401@vu.edu.pk
the
program wants when using
this descriptor. The 13bit
index is the actual
index
into the GDT to select
the appropriate descriptor. 13
bits mean that a
maximum of
8192 descriptors are
possible in the GDT.
The
GDT itself is an array of
descriptors where each
descriptor is an 8byte
entry.
The base and limit of GDT is
stored in a 48bit register
called the
GDTR.
This register is loaded with a
special instruction LGDT and
is given a
memory
address from where the
48bits are fetched. The
first entry of the
GDT
must always be zero. It is called
the null descriptor. After
that any
number
of entries upto a maximum of 8191
can follow. The format of a
code
and
data descriptor is shown
below.
The
32bit base in both
descriptors is scattered into
different places
because
of compatibility reasons. The limit is
stored in 20 bits but the G
bit
defines
that the limit is in terms of
bytes of 4K pages therefore a maximum
of
4GB
size is possible. The P bit must be
set to signal that this
segment is
present
in memory. DPL is the
descriptor privilege level
again related to the
protection
levels in 386. D bit defines
that this segment is to
execute code is
16bit
mode or 32bit mode. C is
conforming bit that we will not be
using. R
signals
that the segment is
readable. A bit is automatically set
whenever the
segment
is accessed. The combination of S
(system) and X (executable)
tell
that
the descriptors is a code or a
data descriptor. B (big) bit
tells that if this
data
segment is used as stack SP is
used or ESP is used.
Our
first example is a very
rudimentary one that just
goes into protected
mode
and prints an A on the
screen by directly accessing
000B8000.
Example
15.1
001
[org
0x0100]
002
jmp
start
003
004
gdt:
dd
0x00000000,
0x00000000
; null
descriptor
005
dd
0x0000FFFF,
0x00CF9A00
; 32bit
code
006
;
\--/\--/
\/||||\/
007
;
|
|
| ||||+--- Base
(16..23)=0 fill later
008
;
|
|
| |||+--- X=1
C=0 R=1 A=0
009
;
|
|
| ||+--- P=1
DPL=00 S=1
010
;
|
|
| |+--- Limit (16..19) =
F
011
;
|
|
| +--- G=1
D=1 r=0 AVL=0
168
Computer
Architecture & Assembly Language
Programming
Course
Code: CS401
CS401@vu.edu.pk
012
;
|
|
+--- Base (24..31)
= 0
013
;
|
+--- Limit (0..15) =
FFFF
014
;
+--- Base
(0..15)=0 fill later
015
dd
0x0000FFFF,
0x00CF9200
; data
016
;
\--/\--/
\/||||\/
017
;
|
|
| ||||+--- Base
(16..23) = 0
018
;
|
|
| |||+--- X=0
E=0 W=1 A=0
019
;
|
|
| ||+--- P=1
DPL=00 S=1
020
;
|
|
| |+--- Limit (16..19) =
F
021
;
|
|
| +--- G=1
B=1 r=0 AVL=0
022
;
|
|
+--- Base (24..31)
= 0
023
;
|
+--- Limit (0..15) =
FFFF
024
;
+--- Base (0..15)
= 0
025
026
gdtreg:
dw
0x17
; 16bit
limit
027
dd
0
; 32bit base
(filled later)
028
029
stack:
times 256 dd 0 ;
for use in p-mode
030
stacktop:
031
032
start:
mov
ax,
0x2401
033
int
0x15
; enable
A20
034
035
xor
eax,
eax
036
mov
ax, cs
037
shl
eax, 4
038
mov
[gdt+0x08+2],
ax
039
shr
eax, 16
040
mov
[gdt+0x08+4],
al
; fill base of
code desc
041
042
xor
edx,
edx
043
mov
dx, cs
044
shl
edx, 4
045
add
edx,
stacktop
; edx = stack top
for p-
046
mode
047
048
xor
eax,
eax
049
mov
ax, cs
050
shl
eax, 4
051
add
eax, gdt
052
mov
[gdtreg+2],
eax
; fill phy
base of gdt
053
lgdt
[gdtreg]
; load gdtr
054
055
mov
eax, cr0
056
or
eax, 1
057
058
cli
; MUST disable
interrupts
059
mov
cr0,
eax
; P-MODE
ON
060
jmp
0x08:pstart
; load cs
061
062
;;;;; 32bit protected
mode ;;;;;
063
064
[bits 32] ; ask
assembler to generate 32bit
code
065
pstart:
mov eax,
0x10
066
mov ds,
ax
067
mov es,
ax
; load other seg
regs
068
mov fs,
ax
; flat memory
model
069
mov gs,
ax
070
mov ss,
ax
071
mov esp,
edx
072
073
mov
byte [0x000b8000],
'A'
; direct poke at
video
074
jmp
$
; hang
around
075
Gate
A20 is a workaround for a
bug that is not detailed
here. The BIOS
call
will
simply enable it to open the
whole memory for us.
Another important
thing
is that the far jump we used
loaded 8 into CS but CS is now a
selector
so it
means Index=1, TI=0, and
RPL=0 and therefore the
actual descriptor
loaded
is the one at index 1 in the
GDT.
169
Computer
Architecture & Assembly Language
Programming
Course
Code: CS401
CS401@vu.edu.pk
15.2.
32BIT PROGRAMMING
Our
next example is to give a
falvour of 32bit programming. We
have
written
the printstr function for
read and for protected
mode. The
availability
of
larger registers and
flexible addressing rules
allows writing a much
comprehensive
version of the code. Also
offsets to parameters and
default
widths
change.
Example
15.2
001
[org
0x0100]
002
jmp
start
003
004
gdt:
dd
0x00000000,
0x00000000
; null
descriptor
005
dd
0x0000FFFF,
0x00CF9A00
; 32bit
code
006
dd
0x0000FFFF,
0x00CF9200
; data
007
008
gdtreg:
dw
0x17
; 16bit
limit
009
dd
0
; 32bit
base
010
011
rstring:
db
'In Real Mode...',
0
012
pstring:
db
'In Protected Mode...',
0
013
014
stack:
times 256 dd
0
; 1K stack
015
stacktop:
016
017
printstr:
push
bp
; real mode print
string
018
mov
bp, sp
019
push
ax
020
push
cx
021
push
si
022
push
di
023
push
es
024
025
mov
di,[bp+4]
;load string
address
026
mov
cx,0xffff
;load maximum
possible size in cx
027
xor
al,al
;clear al
reg
028
repne
scasb
;repeat
scan
029
mov
ax,0xffff
;
030
sub
ax,cx
;calculate
length
031
dec
ax
;off by one, as it includes
zero
032
mov
cx,ax
;move length to
counter
033
034
mov
ax,
0xb800
035
mov
es, ax
; point es to video
base
036
mov
ax,80
;its a word
move, clears ah
037
mul
byte [bp+8]
;its a byte mul to calc y
offset
038
add
ax,[bp+10]
;add x
offset
039
shl
ax,1
;mul by 2 to get
word offset
040
mov
di,ax
;load
pointer
041
042
mov si,
[bp+4]
; string to be
printed
043
mov ah,
[bp+6]
; load
attribute
044
045
cld
; set auto increment
mode
046
nextchar:
lodsb
;load next char
and inc si by 1
047
stosw
;store ax and inc
di by 2
048
loop
nextchar
049
050
pop
es
051
pop
di
052
pop
si
053
pop
cx
054
pop
ax
055
pop
bp
056
ret
8
057
058
start:
push byte
0
; 386
can directly push
059
immediates
060
push
byte 10
061
push
byte 7
062
push
word
rstring
063
call
printstr
064
170
Computer
Architecture & Assembly Language
Programming
Course
Code: CS401
CS401@vu.edu.pk
065
mov
ax,
0x2401
066
int
0x15
; enable
a20
067
068
xor
eax,
eax
069
mov
ax, cs
070
shl
eax, 4
071
mov
[gdt+0x08+2],
ax
072
shr
eax, 16
073
mov
[gdt+0x08+4],
al
; set base of
code desc
074
075
xor
edx,
edx
076
mov
dx, cs
077
shl
edx, 4
078
add
edx,
stacktop
; stacktop to be
used in p-mode
079
080
xor
ebx,
ebx
081
mov
bx, cs
082
shl
ebx, 4
083
add
ebx,
pstring
; pstring to be
used in p-mode
084
085
xor
eax,
eax
086
mov
ax, cs
087
shl
eax, 4
088
add
eax, gdt
089
mov
[gdtreg+2],
eax
; set base of
gdt
090
lgdt
[gdtreg]
; load gdtr
091
092
mov
eax, cr0
093
or
eax, 1
094
095
cli
; disable
interrupts
096
mov
cr0,
eax
; enable protected
mode
097
jmp
0x08:pstart
; load cs
098
099
;;;;; 32bit protected
mode ;;;;;
100
101
[bits 32]
102
pprintstr:
push
ebp
; p-mode print
string routine
103
mov
ebp,
esp
104
push
eax
105
push
ecx
106
push
esi
107
push
edi
108
109
mov edi,
[ebp+8] ;load string address
110
mov ecx,
0xffffffff ;load maximum possible size in
cx
111
xor al,
al
;clear al
reg
112
repne
scasb
;repeat
scan
113
mov eax,
0xffffffff
;
114
sub eax,
ecx
;calculate
length
115
dec
eax
;off by one, as it includes
zero
116
mov ecx,
eax
;move length to
counter
117
118
mov
eax, 80
;its a word
move, clears ah
119
mul
byte
[ebp+16]
;its a byte mul to calc
y
120
offset
121
add
eax,
[ebp+20]
;add x
offset
123
shl
eax,
1
;mul by 2 to get
word offset
124
add
eax,
0xb8000
125
mov
edi,
eax
;load
pointer
126
127
mov esi,
[ebp+8]
; string to be
printed
128
mov ah,
[ebp+12]
; load
attribute
129
130
cld
; set auto increment
mode
131
pnextchar:
lodsb
;load next char
and inc si by 1
132
stosw
;store ax and inc
di by 2
133
loop
pnextchar
134
135
pop
edi
136
pop
esi
137
pop
ecx
138
pop
eax
139
pop
ebp
140
ret
16
; 4 args now
mean 16 bytes
141
171

Computer
Architecture & Assembly Language
Programming
Course
Code: CS401
CS401@vu.edu.pk
142
pstart:
mov
ax,
0x10
; load all seg
regs to 0x10
143
mov
ds, ax
; flat memory
model
144
mov
es, ax
145
mov
fs, ax
146
mov
gs, ax
147
mov
ss, ax
148
mov
esp,
edx
; load saved
esp on stack
149
150
push
byte 0
133
push
byte 11
134
push
byte 7
135
push
ebx
136
call
pprintstr
; call p-mode
print string
137
routine
138
139
mov
eax,
0x000b8000
140
mov
ebx, '/-\|'
141
142
nextsymbol:
mov
[eax], bl
143
mov
ecx,
0x00FFFFFF
144
loop
$
145
ror
ebx, 8
146
jmp
nextsymbol
15.3.
VESA LINEAR FRAME
BUFFER
As an
example of accessing a really
large area of memory for
which
protected
mode is a necessity, we will be accessing
the video memory in
high
resolution
and high color graphics
mode where the necessary
video memory
is
alone above a megabyte. We will be
using the VESA VBE 2.0
for a standard
for
these high resolution
modes.
VESA is
the Video Electronics
Standards Association and VBE is
the set of
Video
BIOS Extensions proposed by
them. The VESA VBE 2.0
standard
includes
a linear frame buffer mode
that we will be using. This
mode allows
direct
access to the whole video
memory. Some important VESA
services are
listed
below.
INT 10 VESA
Get
SuperVGA
Infromation
AX =
4F00h
ES:DI -> buffer for
SuperVGA information
Return:
AL = 4Fh if
function supported
AH = status
INT 10 VESA
Get SuperVGA Mode
Information
AX =
4F01h
CX = SuperVGA
video mode
ES:DI ->
256-byte buffer for mode
information
Return:
AL = 4Fh if
function supported
AH = status
ES:DI filled if no
error
INT 10 VESA
Set VESA Video
Mode
AX =
4F02h
BX = new video
mode
Return:
AL = 4Fh if
function supported
AH = status
One of
the VESA defined modes is
8117 which is a 1024x768 mode
with
16bit
color and a linear frame
buffer. The 16 color bits
for every pixel
are
organized
in 5:6:5 format with 5 bits
for red, 6 for green,
and 5 for blue.
This
makes
32 shades of red and blue
and 64 shades of green and
64K total
172
Computer
Architecture & Assembly Language
Programming
Course
Code: CS401
CS401@vu.edu.pk
possible
colors. The 32bit linear
frame buffer base address is
available at
offset
28 in the mode information
buffer. Our example will produces
shades
of
green on the screen and
clear them and again print
them in an infinite
loop
with delays in between.
Example
15.3
001
[org
0x0100]
002
jmp
start
003
004
modeblock:
times 256 db
0
005
006
gdt:
dd
0x00000000,
0x00000000
; null
descriptor
007
dd
0x0000FFFF,
0x00CF9A00
; 32bit
code
008
dd
0x0000FFFF,
0x00CF9200
; data
009
010
gdtreg:
dw
0x17
; 16bit
limit
011
dd
0
; 32bit
base
012
013
stack:
times 256 dd
0
; 1K stack
014
stacktop:
015
016
start:
mov
ax,
0x4f01
; get vesa
mode information
017
mov
cx,
0x8117
; 1024*768*64K
linear frame
018
buffer
019
mov
di,
modeblock
020
int
0x10
021
mov
esi,
[modeblock+0x28]
; save
frame buffer base
022
023
mov
ax,
0x4f02
; set vesa
mode
024
mov
bx,
0x8117
025
int
0x10
026
027
mov
ax,
0x2401
028
int
0x15
; enable
a20
029
030
xor
eax,
eax
031
mov
ax, cs
032
shl
eax, 4
033
mov
[gdt+0x08+2],
ax
034
shr
eax, 16
035
mov
[gdt+0x08+4],
al
; set base of
code desc
036
037
xor
edx,
edx
038
mov
dx, cs
039
shl
edx, 4
040
add
edx,
stacktop
; stacktop to be
used in p-mode
041
042
xor
eax,
eax
043
mov
ax, cs
044
shl
eax, 4
045
add
eax, gdt
046
mov
[gdtreg+2],
eax
; set base of
gdt
047
lgdt
[gdtreg]
; load gdtr
048
049
mov
eax, cr0
050
or
eax, 1
051
052
cli
; disable
interrupts
053
mov
cr0,
eax
; enable protected
mode
054
jmp
0x08:pstart
; load cs
055
056
;;;;; 32bit protected
mode ;;;;;
057
058
[bits 32]
059
pstart:
mov
ax,
0x10
; load all seg
regs to 0x10
060
mov
ds, ax
; flat memory
model
061
mov
es, ax
062
mov
fs, ax
063
mov
gs, ax
064
mov
ss, ax
065
mov
esp,
edx
; load saved
esp on stack
066
067
l1:
xor
eax,
eax
173
Computer
Architecture & Assembly Language
Programming
Course
Code: CS401
CS401@vu.edu.pk
068
mov
edi, esi
069
mov
ecx,
1024*768*2/4
; divide by 4 as
dwords
070
cld
071
rep
stosd
072
073
mov
eax,
0x07FF07FF
074
mov
ecx, 32
; no of
bands
075
mov
edi, esi
076
077
l2:
push
ecx
078
mov ecx,
768*16
; band width =
32
079
lines
080
cld
081
rep stosd
082
083
mov ecx,
0x000FFFFF
; small
wait
084
loop $
085
pop
ecx
086
087
sub eax,
0x00410041
088
loop l2
089
090
mov ecx,
0x0FFFFFFF
; long wait
091
loop $
092
jmp
l1
093
15.4.
INTERRUPT HANDLING
Handling
interrupts in protected mode is
also different. Instead of
the IVT
at
physical address 0 there is
the IDT (interrupt descriptor
table) located at
physical
address stored in IDTR, a
special purpose register.
The IDTR is also
a 48bit
register similar in structure to
the GDTR and loaded with
another
special
instruction LGDT. The format
of the interrupt descriptor is as
shown
below.
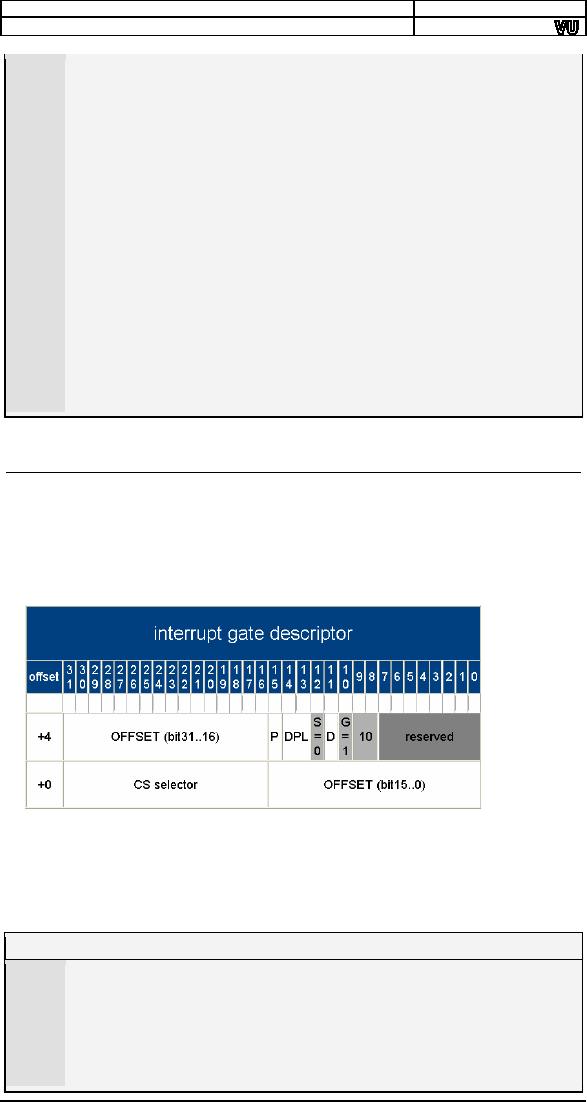
The P
and DPL have the
same meaning as in data and
code descriptors.
The S
bit tells that this is a
system descriptor while the
1110 following it
tells
that it
is a 386 interrupt gate. Our
example hooks the keyboard
and timer
interrupts
and displays certain things
on the screen to show that
they are
working.
Example
15.4
001
[org
0x0100]
002
jmp
start
003
004
gdt:
dd
0x00000000,
0x00000000
; null
descriptor
005
dd
0x0000FFFF,
0x00CF9A00
; 32bit
code
006
dd
0x0000FFFF,
0x00CF9200
; data
007
008
gdtreg:
dw
0x17
; 16bit
limit
009
dd
0
; 32bit
base
174
Computer
Architecture & Assembly Language
Programming
Course
Code: CS401
CS401@vu.edu.pk
010
011
idt:
times 8 dw unhandled,
0x0008, 0x8e00,
0x0000
012
dw
timer, 0x0008,
0x8e00, 0x0000
013
\---/
\----/
||\/
\----/
014
|
|
|| |
+----- offset bits
16..32
015
|
|
|| +-----
reserved
016
|
|
|+------ Type=E
386 Interrupt Gate
017
|
|
+--- P=1
DPL=00 S=0
018
|
+-------
selector
019
+-------- offset bits
0..15
020
dw
keyboard,
0x0008, 0x8e00,
0x0000
021
times 246 dw
unhandled, 0x0008, 0x8e00,
0x0000
022
023
idtreg:
dw
0x07FF
024
dd
0
025
026
stack:
times 256 dd
0
; 1K stack
027
stacktop:
028
029
start:
mov
ax,
0x2401
030
int
0x15
; enable
a20
031
032
xor
eax,
eax
033
mov
ax, cs
034
shl
eax, 4
035
mov
[gdt+0x08+2],
ax
036
shr
eax, 16
037
mov
[gdt+0x08+4],
al
; set base of
code desc
038
039
xor
edx,
edx
040
mov
dx, cs
041
shl
edx, 4
042
add
edx,
stacktop
; stacktop to be
used in p-mode
043
044
xor
eax,
eax
045
mov
ax, cs
046
shl
eax, 4
047
add
eax, gdt
048
mov
[gdtreg+2],
eax
; set base of
gdt
049
lgdt
[gdtreg]
; load gdtr
050
051
xor
eax,
eax
052
mov
ax, cs
053
shl
eax, 4
054
add
eax, idt
055
mov
[idtreg+2],
eax
; set base of
idt
056
057
cli
; disable
interrupts
058
lidt
[idtreg]
; load idtr
059
060
mov
eax, cr0
061
or
eax, 1
062
mov
cr0,
eax
; enable protected
mode
063
064
jmp
0x08:pstart
; load cs
065
066
;;;;; 32bit protected
mode ;;;;;
067
068
[bits 32]
069
unhandled:
iret
070
071
timer:
push
eax
072
073
inc
byte
[0x000b8000]
074
075
mov al,
0x20
076
out 0x20,
al
077
pop
eax
078
iret
079
080
keyboard:
push
eax
081
082
in
al,
0x60
083
mov
ah,
al
084
and
al,
0x0F
085
shr
ah,
4
175

Computer
Architecture & Assembly Language
Programming
Course
Code: CS401
CS401@vu.edu.pk
086
add
ax,
0x3030
087
cmp
al,
0x39
088
jbe
skip1
089
add
al, 7
090
skip1:
cmp
ah,
0x39
091
jbe
skip2
092
add
ah, 7
093
skip2:
mov
[0x000b809C],
ah
094
mov
[0x000b809E],
al
095
096
skipkb:
mov al,
0x20
097
out 0x20,
al
098
pop
eax
099
iret
100
101
pstart:
mov
ax,
0x10
; load all seg
regs to 0x10
102
mov
ds, ax
; flat memory
model
103
mov
es, ax
104
mov
fs, ax
105
mov
gs, ax
106
mov
ss, ax
107
mov
esp,
edx
; load saved
esp on stack
108
109
mov
al,
0xFC
110
out
0x21, al
; no unexpected
int comes
111
112
sti
; interrupts are
okay now
113
114
jmp
$
EXERCISES
1.
Write very brief and
to-the-point answers.
a. Why
loading idtr with a value
appropriate for real mode
is
necessary
while gdtr is not?
b. What
should we do in protected mode so
that when we turn
protection
off, we are in unreal
mode?
c. If
the line jmp code:next is
replaced with call
code:somefun,
the
prefetch queue is still
emptied. What problem will
occur
when
somefun will return?
d. How much is
ESP decremented when an interrupt
arrives.
This
depends on weather we are in
16-bit mode or
32-bit.
Does it
depend on any other thing as
well? If yes, what?
e. Give
two instructions that change
the TR register.
2. Name
the following descriptors
like code descriptor, data
descriptor,
interrupt
gate etc.
gdt:
dd
0x00000000,
0x00000000
dd
0x00000000,
0x00000000
dd
0x80000fA0,
0x0000820b
dd
0x0000ffff,
0x00409a00
dd
0x80000000,
0x0001d20b
3.
Using the above GDT, which
of the following values, when
moved into
DS will
cause an exception and
why.
0x00
0x08
0x10
0x18
0x28
0x23
4.
Using the above GDT, if DS
contains 0x20, which of the
following
offsets
will cause an exception on read
access?
0x0ffff
0x10000
0x10001
176

Computer
Architecture & Assembly Language
Programming
Course
Code: CS401
CS401@vu.edu.pk
5. The
following function is written in
32-bit code for a 16-bit
stack.
Against
every instruction, write the
prefixes generated before
that
instruction.
Prefixes can be address
size, operand size, repeat,
or
segment
override. Then rewrite the
code such that no prefixes
are
generated
considering that this is
assembled and executed in
32-bit
mode.
Don't care for retaining
register values. The
function copies
specified
number of DWORDs between two
segments.
[bits 32]
memcpy:
mov
bp, sp
lds
esi, [bp+4]
;
source
address
les
edi,
[bp+10]
;
destination
address
mov
cx, [bp+16]
;
count of DWORDs to
move
shl
cx, 1
;
make into count of
WORDs
L1:
mov
dx, [si]
mov
[es:di], dx
dec
cx
jnz
L1
ret
6.
Rewrite the following
scheduler so that it schedules
processes stored
in
readyQ, where enque and
deque functions are
redefined and
readyQ
contains TSS selectors of
processes to be multitasked.
Remember
you can't use a register as
a segment in a jump (eg jmp
ax:0)
but you can jump to an indirect
address (eg jmp far [eax])
where
eax
points to a six-byte address.
Declare any variables you
need.
mov al,
0x20
scheduler:
jmp
USERONESEL:0
out 0x20,
al
mov byte
[USERONEDESC+5], 0x89
jmp
USERTWOSEL:0
out 0x20,
al
mov byte
[USERTWODESC+5], 0x89
jmp
scheduler
7. Protected
mode has specialized
mechanism for multitasking
using task state
segments
but the method used in
real mode i.e. saving
all registers in a
PCB,
selecting
the next PCB and
loading all registers from
there is still
applicable.
Multitask
two tasks in protected mode
multitasking without TSS.
Assume that
all
processes are at level zero
so no protection issues arise. Be
careful to
save the
complete state of the
process.
8. Write
the following
descriptors.
a. 32 bit,
conforming, execute-only code
segment at level 2, with
base
at 6MB and
a size of 4MB.
b. 16 bit,
non-conforming, readable code
segment at level 0, with
base
at 1MB and
a size of 10 bytes.
c. Read
only data segment at level
3, with base at 0 and size
of 1MB.
d. Interrupt
Gate with selector 180h
and offset 11223344h.
9. Write
physical addresses for the
following accesses where CS
points to the
first
descriptor above, DS to the
second, ES to the third, EBX
contains
00010000h,
and ESI contains
00020000h
a.
[bx+si]
b.
[ebx+esi-2ffffh]
c.
[es:ebx-10h]
10. Which
of the following will cause
exceptions and why. The
registers have the
same
values as the last
question.
a. mov
eax, [cs:10000h]
b. mov
[es:esi:100h], ebx
c. mov ax,
[es:ebx]
11.
Give short answers.
a. How
can a GPF (General
protection fault) occur
while running
the
following code
push
es
pop
es
177

Computer
Architecture & Assembly Language
Programming
Course
Code: CS401
CS401@vu.edu.pk
b. How
can a GPF occur during
the following instruction?
Give
any two
reasons.
jmp
10h:100h
c. What
will happen if we call interrupt 80h
after loading out IDT
and
before switching to protected
mode?
d. What
will happen if we call interrupt 80h
after switching into
protected
mode but before making a far
jump?
12.
Write the following
descriptors. Assume values
for attributes not
specifically
mentioned.
a.
Write able 32-bit data
segment with 1 GB base and 1 GB
limit
and a
privilege level of 2.
b.
Readable 16-bit code
descriptor with 1 MB base and 1
MB
limit
and a privilege level of
1.
c.
Interrupt gate given that
the handler is at 48h:12345678h
and
a
privilege level of 0.
13.
Describe the following
descriptors. Give their type
and the value of
all
their
fields.
dd 01234567h,
789abcdeh
dd 30405060h,
70809010h
dd 00aabb00h,
00ffee00h
14.
Make an EXE file, switch
into protected mode, rotate
an asterisk on
the
border of the screen, and
return to real mode when the
border is
traversed.
178
Table of Contents:
- Introduction to Assembly Language Programming
- Addressing Modes: Data Declaration, Direct, Register Indirect , Offset Addressing
- Branching: Comparison and Conditions, Conditional ,Unconditional Jump
- Manipulations: Multiplication Algorithm, Shifting and Rotations, Bitwise Logical Operations
- Subroutines: Program Flow, Stack, Saving and Restoring Registers
- Display Memory: ASCII Codes, Display Memory Formation, Assembly Language
- String Instructions: String Processing, Clearing Screen, String Printing, Length
- Software Interrupts: Hooking an Interrupt, BIOS and DOS Interrupts
- Real Time Interrupts and Hardware Interfacing
- Debug Interrupts: Debugger using single step interrupt, breakpoint interrupt
- Multitasking: Concept, Elaborate, Multitasking Kernel as TSR
- Video Services: BIOS Video Services, DOS Video Services
- Secondary Storage: Storage Access Using BIOS, DOS, Device Drivers
- Serial Port Programming: Serial Communication
- Protected Mode Programming: VESA Linear Frame Buffer, Interrupt Handling
- Interfacing with High Level Languages: Calling Conventions, Calling C from Assembly
- Comparison: Motorolla 68K Processors, Sun SPARC Processor