 |
COMPUTER NETWORKS: types of networks, networking topologies and protocols |
| << ARRAYS |
| THE INTERNET >> |
Introduction
to Computing CS101
VU
LESSON
27
COMPUTER
NETWORKS
During
the last Lesson ...
(Web
Design for
Usability)
�
We
looked at the role of usability in Web
design
�
We
identified some of the factors affecting
the usability of a Web page
Designs
should be consistent
&
predictable (unified)
What's
a Good Site?
�
The
one that achieves the result
that it was designed
for
�
Generally,
that result can only be
achieved by giving the user what
s/he wants, as quickly as
possible,
without her/im expending
much effort
�
One
definition of usability: Let the
user have what s/he wants,
quickly, without much
effort
�
"Quickly"
is important!
Website
Navigation
�
It
probably is the most important
aspect of the design of a Website
Good
designs assist the user in
recovering from errors
Today's
Goals:
(Computer
Networks)
�
We
will become able to appreciate the
role of networks in
computing
�
We
will look at several different types of
networks
�
We
will familiarize ourselves with
networking topologies and
protocols
Computer
Network
Multiple
computers that are connected
together to share information and
other resources
Examples of
Computer Network
Usage
�
I can
send an eMail message to a remote
computer using the SMTP
protocol
�
I can
browse documents residing on a remote computer
using the HTTP
protocol
�I
can download or upload
files to a remote computer using the FTP
protocol
�I
can run a program on a remote
computer using the TELNET
protocol
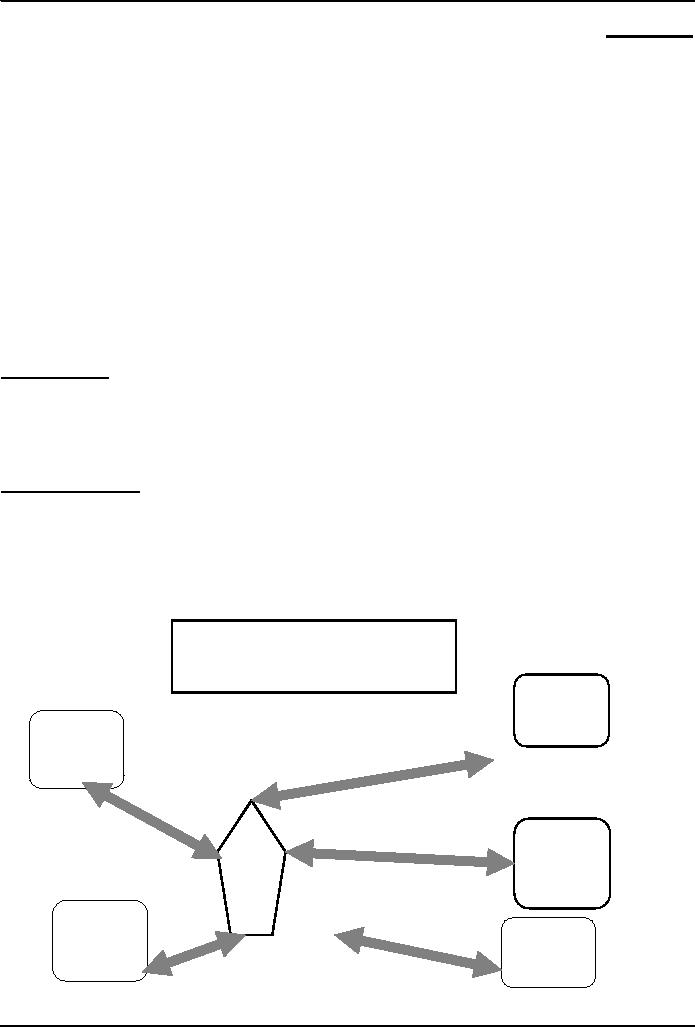
Example of a
Computer
Network
Computer
E
Computer
A
Computer
Hub
D
Computer
Computer
B
C
Components of
Conventional Computer
Networks
1.
Computers
2.
Network Interface Cards
(NIC)
I/O
device that plugs into the
computer
173

Introduction
to Computing CS101
VU
Enables
it to communicate over a network
3.
Hub
The
network traffic
controller
Components of
Conventional Computer
Networks
4.Cables
Are
either electrical or
optical
Not
required at all for wireless
networks
5.Protocol
Rules
governing communications over the
network
How
Does a Conventional Network
Work?
1.
Suppose computer A wants to send a
message to D
2.
Computer A sends the message to
its NIC
3.
The NIC translates the message
into electrical pulses
suitable for the computer network in
use &
transmits it to
the hub through the cable
4.
The hub receives them and
forwards them to all computers
connected to the it
5.
The NICs of all
computers connected to the hub receive
the forwarded electrical
pulses
6.
The NIC of computer D decides that
the message is for it, &
translates the pulses back to a
form
suitable
for the computer
Hub
�
A
device that is used to
connect several computers to form a
network
�
A hub
has several ports. The number generally
is 8, 12, 16, 24, 32, or
48
�
Each
computer in a network is connected to one
of those ports through a cable
�
A computer
wanting to send a message to one of the
others in the network sends a
message to the
hub,
which, in turn, broadcasts the
message to all others
connected to it
Packet
�
The
smallest unit of data
transmitted over a computer
network
�
A
message to be transferred over the
network is broken up into
small packets by the sending
computer
�
Each
packet contains the following
info:
Sender's
address
Destination
address
Data
Error-recovery
info
�
All
packets travel
independently
�
When
all packets are received by
the destination computer, it reassembles them to
form the original
message
Types
of Computer Networks
according to
the network access
policy
�
Private
�
Public
27.1
Private Networks
�
Organizations
having many computers
usually connect them in the form of
private networks
�
Access
to these network is restricted to
authorized computers
only
�
Organizations
having many computers
usually connect them in the form of
private networks
�
Access
to these network is restricted to
authorized computers
only
�
This
allows computers from within
the organization to exchange info, but
keeps the info
private
and protected
from outsiders
�
All
equipment on a private network is
generally for the exclusive
use of that
organization
27.2
Public Networks
�
All
networks that are not
private, are ...
public
174
Introduction
to Computing CS101
VU
�
Example:
Internet
�
Communication
equipment used in these
networks is generally being
used by users belonging
to
several
(possibly thousands of)
organizations as well as those
belonging to no organization
27.3
VPN: Virtual Private Network
(1)
�
From
the user's point-of-view, a VPN looks
like a secure, private
network
�
VPNs
use public telecom infrastructure,
maintaining privacy through
security procedures
�
VPNs
provide secure network connections
for distance computers
without using dedicated,
private
channels
to supply the connection
�
Key
benefit of VPNs over
conventional PNs: Lower
cost
Types
of Computer Networks
according to
the distance between
nodes
LAN:
Local Area Network)
WAN:
Wide Area Network)
LAN
A
network of computers located in the
same building or a handful of
nearby buildings
Examples:
Computer
network at your PVC
Computer
network of a University
campus
WAN
A
network in which computers
are separated by great distances,
typically across cities or
even
continents
May
consist of several interconnected
LANs
Example:
The
network connecting the ATM of a
bank located in various
cities
A
network connecting the local and
oversea offices of a SW
house
Internet
Connecting
LANs to other
Networks:
Special-purpose
devices are used to link
LANs to other
networks
They
may belong to one of the following
categories:
Routers
Bridges
Gateways
Modems
Router
A special-purpose
computer that directs data traffic
when several paths are
available
A
router examines the destination
info in each arriving packet and
then routes it through the
most
efficient
path available
The
router either delivers the packet to the
destination computer across a local
network or forwards the
packet to another
router that is closer to the
final destination
Bridge
Used to
form a connection between two
separate, but similar
networks
In a
way, it creates an extended LAN by
passing information between two or more
LANs
Gateway
A special-purpose
computer that connects and translates
between networks that use
different
communications
protocols
LAN's
may use a gateway (or
router) to connect to the
Internet
175
Introduction
to Computing CS101
VU
Modem
I/O
device used for connecting
two computers over telephone
lines
modem
= modulator + demodulator
Modulator
converts computer messages to electrical
pulses that are suitable
for transmission over the
telephone
lines
Demodulator
converts electrical pulses received
over telephone lines into
messages that are
comprehensible
for computers
27.4
Network Topologies
The
pattern in which computers
are connected to form a
network
Popular
patterns:
Point-to-point
Star
Bus
Ring
Networks
are also formed by combining
2 or more of these 4 basic
patterns
P2P
Inexpensive
LimitedComnecttivity
con pu er
Computer
B
A
Quite
often used for connecting
two LANs to form a
WAN
Star
A computer
sends the address of the intended
receiver and the data to the
server
The
server then sends the
message to the intended
receiver
This
topology allows multiple
messages to be sent
simultaneously
Costly,
because it uses an additional computer to
direct the data
Costly,
because each node is individually
wired to the hub
If the
server goes down, so does
the network
If
any of the nodes goes down,
the rest of the network is not
affected
Computer
D
Star
Computer
Computer
A
C
Server
Computer
B
Bus
No
server is required
One
computer sends data to another by broadcasting the
address of the receiver and the
data over the
bus
176
Introduction
to Computing CS101
VU
All the
computers in the network look at the
address simultaneously, and the intended
recipient accepts
the
data
A bus
network, unlike ring or star
networks, allows data to be
sent directly from one computer
to
another
However,
only one computer at a time can
transmit data. The others
must wait to until the bus
gets idle
If
any of the nodes goes down,
the rest of the network is not
affected
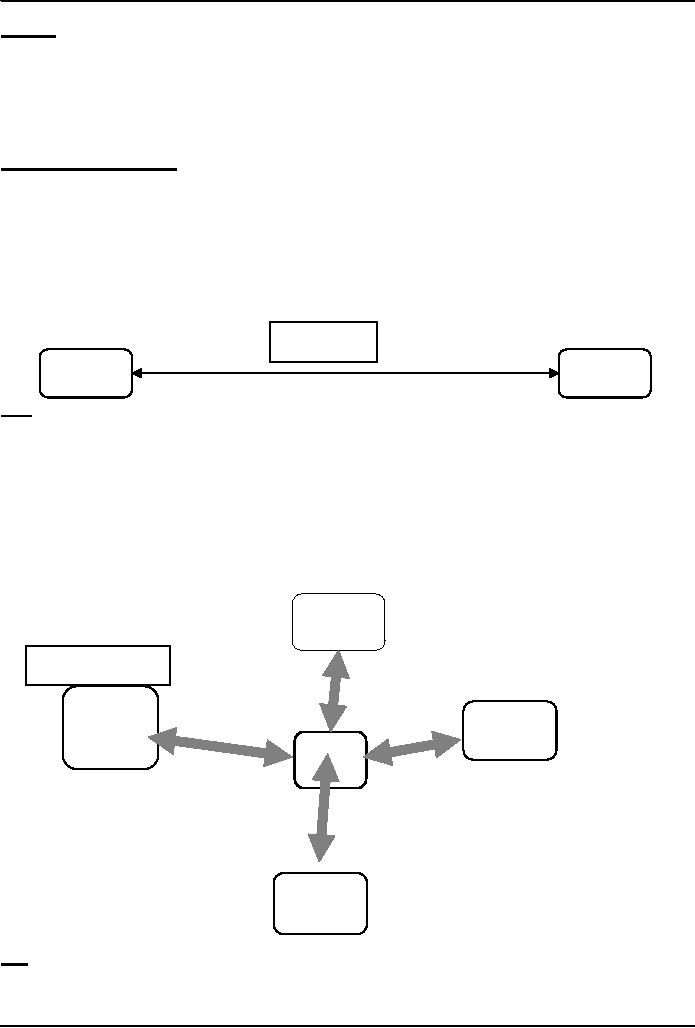
Bus
Computer
Computer
Computer
B
C
A
Computer
Bus: A
high speed
D
Ring
cable
No
server is required
A computer
sends the message to its
neighbor. The neighbor
examines the message to determine if it
is
the
intended recipient
If the
data are not intended
for that particular
neighbor, it passes the message to the
next computer in the
ring
This
process is repeated until the
data arrive at their
intended recipient
This
topology allows multiple
messages to be carried,
simultaneously
Data transmission
is slow since each message
is checked by each computer
New
nodes are difficult to
add
Messages
propagate in one direction only
Compu
The
network fails if a single node
fails
Compu
ter
Compu
Compu
ter
177
Introduction
to Computing CS101
VU
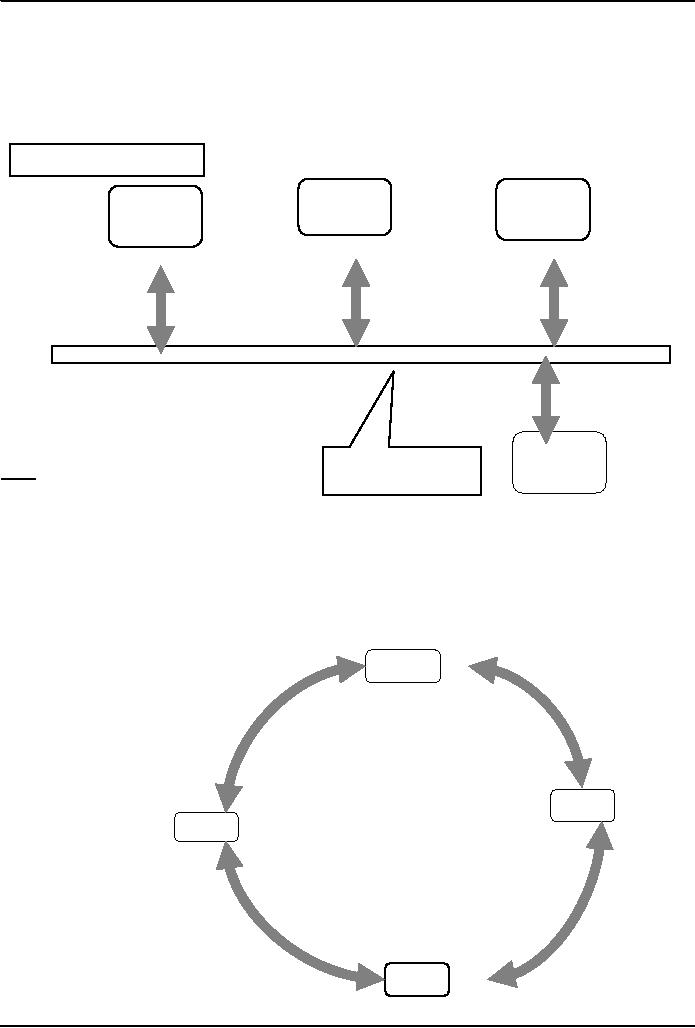
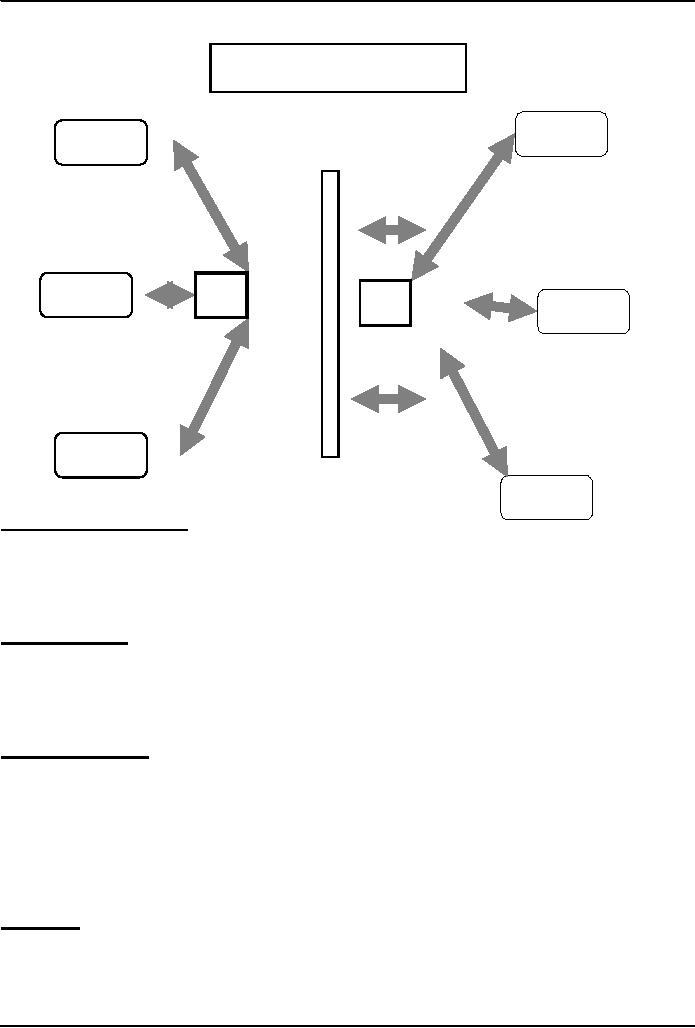
Combination
Computer
Computer
D
A
Hub
Computer
Hub
Computer
B
E
Computer
C
Computer
F
27.5
Networking Protocols
Networks
use protocols, or rules, to exchange info
through shared
channels
Protocols
prevent collisions of packets
caused by simultaneous transmission between two or
more
computers
Several
protocols are available for
various types of networks. Here we
discuss two that are
popular for
LANs:
Ethernet; Token Ring
Ethernet
Protocol
A computer
using this protocol checks
if a shared connection is in use
before transmitting a
message
If
not, the computer transmits data
Two
computers may sense an idle
connection and may send
packets simultaneously. To account
for
such
situations, transmitting computers
continue to monitor the connection and
re-transmit if a packet
collision
occurs
Token
Ring Protocol
This
protocol passes a special message
called a token through the
network
A computer
that receives the token is
given permission to send a packet of
information
If the computer
has no packet to send, it passes the
token to the next computer
Computer
Networks = Computers +
Communications
Types of
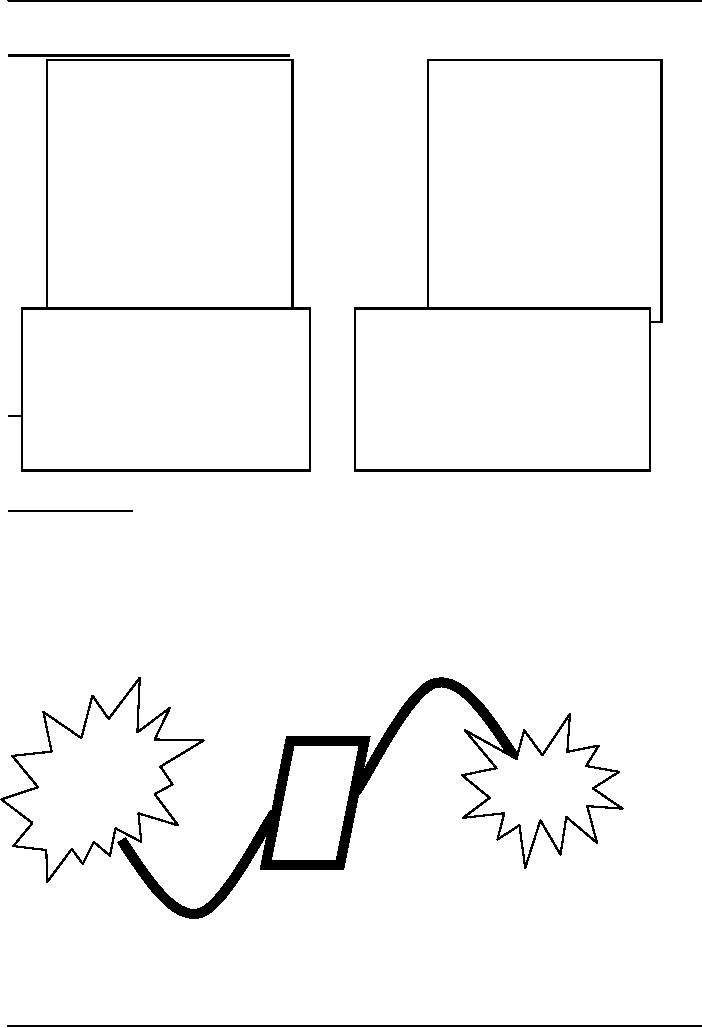
Communication Channels
1 .
Wire
2 .
Wireless
A key
characteristic of these channels is
bandwidth
Bandwidth
Capacity
of a communication channel for carrying
data
Measured
in bits/s (bps), kb/s, Mb/s, Gb/s,
Tb/s
Optical
fiber channels have the highest (1
Tb/s)
Telephone
lines the lowest (56
kb/s)
178
Introduction
to Computing CS101
VU
27.6
Types of Communication
Channels
Wire
Wireless
Copper
Line-of-sight
� Twisted-
� Microwa
pair
ve
� Coaxial
� Optical
cable
Non-line-of-
Optical
fiber
sight
� Satellite
� Radio
� Cellular
Wireless
(Radio) LANs Are Becoming
Popular
Key
benefits:
Key
challenges:
Security &
privacy
Set-up
time
Quality of
service
Set-up
cost
Cost
Maintenance
cost
27.7
Network Security
Keepin an eoston the
security of private networks (e.g.
LANs) is relatively
easy
g C ye
However,
their connections to other networks (e.g.
the Internet) pose a security
risk because the one
has
no
control over users on those
networks
Network
Security
Applications
transferred from the Internet to the LAN
may contain computer viruses
External,
unauthorized users may gain
access to sensitive
data
A special
type of gateway - a firewall
can keep external users from
accessing resources on the LAN
while
letting LAN users access the
external info
Firewall
A
system that that guards a
private network, enforcing an
access/deny policy to all
traffic going to and
coming
from the Internet
It
keeps an eye on all the packets
that go in and out of the private
network and blocks them or
allows
them to
continue to their destination
according to the policy
Internet
Private
Firewall
Network
Firewall
Policy: Example
One
can configure a firewall to
allow only eMail to enter the
private network, thus
shielding it from any
malicious
attacks except for those via
eMail
179

Introduction
to Computing CS101
VU
In
Today's Lecture:
We
looked at the role of networks in
computing
We
looked at several different types of
networks
We
familiarized ourselves with networking
topologies and protocols
Next
Lecture:
Introduction
to the Internet
To
become able to appreciate the role of the
Internet in today's
computing
To
become familiar with the
history and evolution of the
Internet
180
Table of Contents:
- INTRODUCTION
- EVOLUTION OF COMPUTING
- World Wide Web, Web’s structure, genesis, its evolution
- Types of Computers, Components, Parts of Computers
- List of Parts of Computers
- Develop your Personal Web Page: HTML
- Microprocessor, Bus interface unit, Data & instruction cache memory, ALU
- Number systems, binary numbers, NOT, AND, OR and XOR logic operations
- structure of HTML tags, types of lists in web development
- COMPUTER SOFTWARE: Operating Systems, Device Drivers, Trialware
- Operating System: functions, components, types of operating systems
- Forms on Web pages, Components of Forms, building interactive Forms
- APPLICATION SOFTWARE: Scientific, engineering, graphics, Business, Productivity, Entertainment, Educational Software
- WORD PROCESSING: Common functions of word processors, desktop publishing
- Interactivity to Forms, JavaScript, server-side scripts
- ALGORITHMS
- ALGORITHMS: Pseudo code, Flowcharts
- JavaScript and client-side scripting, objects in JavaScript
- Low, High-Level, interpreted, compiled, structured & object-oriented programming languages
- Software Design and Development Methodologies
- DATA TYPES & OPERATORS
- SPREADSHEETS
- FLOW CONTROL & LOOPS
- DESIGN HEURISTICS. Rule of thumb learned through trial & error
- WEB DESIGN FOR USABILITY
- ARRAYS
- COMPUTER NETWORKS: types of networks, networking topologies and protocols
- THE INTERNET
- Variables: Local and Global Variables
- Internet Services: FTP, Telnet, Web, eMail, Instant messaging, VoIP
- DEVELOPING PRESENTATIONS: Effective Multimedia Presentations
- Event Handlers
- GRAPHICS & ANIMATION
- INTELLIGENT SYSTEMS: techniques for designing Artificial Intelligent Systems
- Mathematical Functions in JavaScript
- DATA MANAGEMENT
- DATABASE SOFTWARE: Data Security, Data Integrity, Integrity, Accessibility, DBMS
- String Manipulations:
- CYBER CRIME
- Social Implications of Computing
- IMAGES & ANIMATION
- THE COMPUTING PROFESSION
- THE FUTURE OF COMPUTING
- PROGRAMMING METHODOLOGY
- REVIEW & WRAP-UP of Introduction to Computing