 |
VIRTUAL PIN PAYMENT SYSTEM |
| << SYMMETRIC KEY ALGORITHMS |
| E-CASH PAYMENT SYSTEM 1 >> |
E-COMMERCE
IT430
VU
Lesson
25
VIRTUAL
PIN PAYMENT SYSTEM
A
Virtual PIN can become
compromised as a result of eavesdropping
and bogus purchases are
possible
before it is
blacklisted. Stolen credit card number
can also be used to set up
Virtual PIN associated
with
email
addresses controlled by the attacker to
carry out bogus
transactions. After every 90
days buyer's credit
card
account is billed for the
charges that have
accumulated and the merchant's
account is credited
accordingly.
FV does accounting for
merchant and buyer; therefore, it
takes a commission per
transaction
according
to its policy.
Advantages
and disadvantages
Simplicity
and no encryption is the biggest
advantage of this payment system,
which means that no
special
software
is needed at the frond end.
This payment system is good
for low-cost information
items.
Therefore, it is
suitable for buying online
articles/journals/music etc. where the
cost of the items is
not
much.
In that eventuality, only sales
are lost rather than actual financial
loss to the merchant if there is
a
fraud. In
other words, only some
extra copies of the information
items are made in case of a
fraud. On the
other
hand merchant is exposed to much
greater financial loss if the
purchase relates to the actual
physical
goods.
One of the disadvantages of this payment model is
that pre-registration of the buyer and
the
merchant
with FV is mandatory in this set up.
Moreover, maintaining a bank account (in
case of merchant)
and
having a credit card (in case of a buyer)
is also essential part of this
system. One can say that
the
merchant
side is less secured in the
transaction because the goods
are delivered by the merchant before
the
payment
is actually received. The
popularity of this payment system
declined after 1998 mainly because
of
the
introduction and development of
encryption based payment
mechanisms.
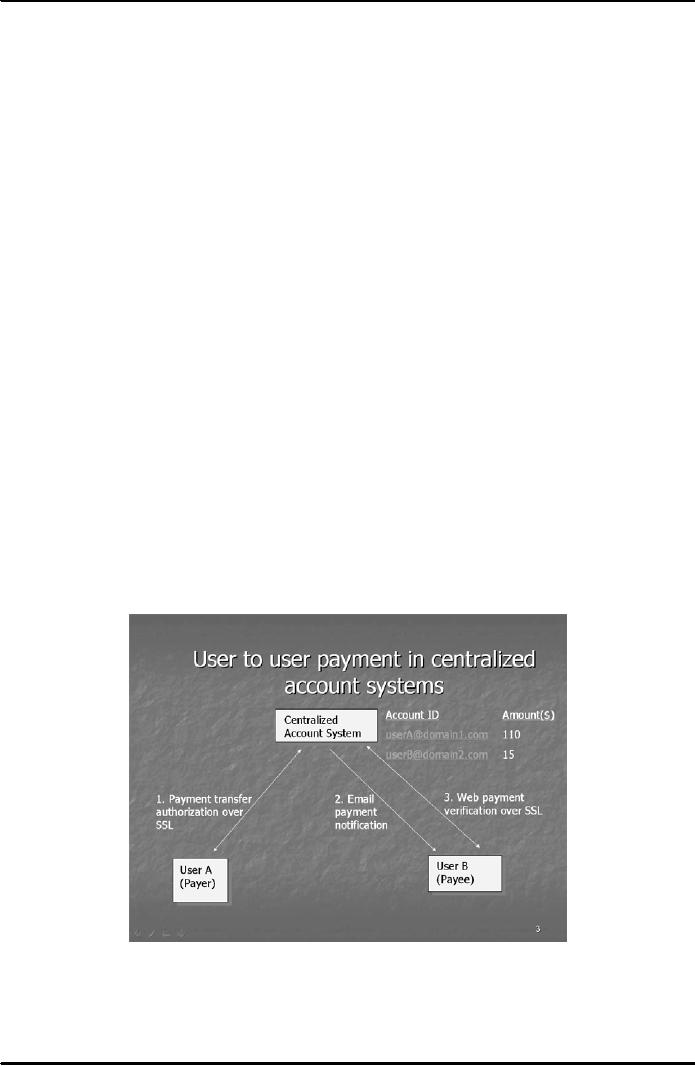
Centralized
Account Payment
Model
This
is a popular payment system on the
internet. In this both the payer (buyer)
and the payee
(merchant)
hold
accounts at the same centralized
on-line financial institution. Over 20
payment systems use
this
approach
e.g., PayPal, E-gold,
Billpoint, Cybergold, Yahoo! Pay Direct,
Amazon.com Payments etc.
This
model is
shown in Fig. 1 below:
Fig.
1
On-line
opening/funding of one's account is done
in a centralized bank using credit/debit
card or prepaid
cards.
To make payment an account
holder is authenticated using an
account identifier and a
password,
account
identifier of the payee and the
payment amount. All communication between
the user and the bank
is protected
using SSL
(Secure Socket Layer), which is an
encryption based protocol.
The chosen account
112
E-COMMERCE
IT430
VU
identifier
or the account ID is the one which is
unique within the system against
which the funds are
lying
in the
online bank. Normally, the unique email
addresses of the users are
chosen as account identifiers.
Payees
are notified by email of the
payment which they can
confirm by viewing their
account using SSL. A
payee
must open an account with the
online centralized bank to receive the
amount in case there is no
such
account
already. In some payment
systems which use this
approach a question may be sent to the
payee to
verify
his identity where the payer
is not sure of that. For
instance, Yahoo Paydirect
allows a payer-specified
question to be
sent to the so called email of the
payee. If the payer accepts the
answer as proof of the
correct
identity of the payee the money is
transferred otherwise the transaction is
cancelled.
The
centralized bank (depending upon its
policy) charges a transaction
fees either from the payer, or
payee
or
both on funding an account or
withdrawing funds from an account or
receiving payments by the
payee/merchant.
This payment model requires that
all participants must have
their account with the
same
central
payment system/bank. Note that the
payee can eventually withdraw the
money received in his
account
in the centralized bank through Automated
Clearing House (ACH).
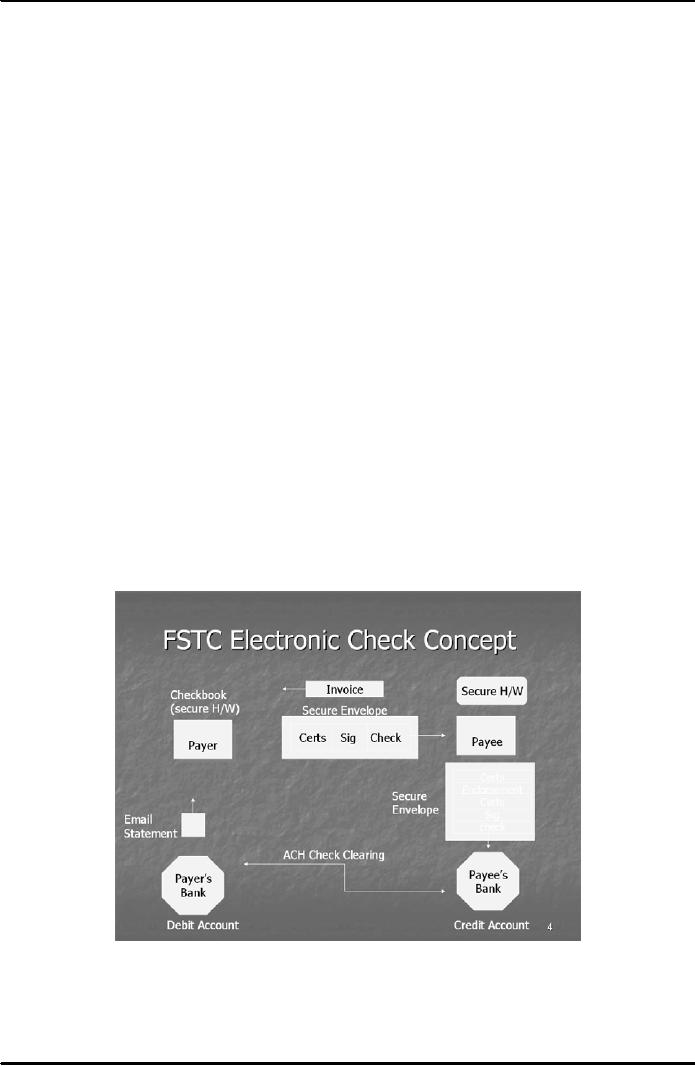
Electronic
Checks
Financial
Services Technology Consortium (FSTC) is a
group of U.S banks, research
agencies and
government
organizations formed in 1993. It
has introduced the concept of electronic
checks. An electronic
check
contains an instruction to the payer's
bank to make a specified payment to a
payee. Both,
symmetric
and
asymmetric type of cryptography is used in this
system. The payer and the
payee are issued
digital
certificates
in X. 509 standard format by
their respective banks.
These certificates are used
to verify the
digital
signatures on the check. A bank may
include account restrictions, maximum
check value, or
currencies
allowed by the bank in the certificate.
All
individuals capable of issuing electronic
checks will have an electronic
check book device. An
electronic
check
book device is a combination of
secure hardware such as a
smart card and appropriate
software. A
smart
card is usually the size of a credit
card having special software
loaded on it. Information
regarding
secret/private
key, certificate information and
register of what checks have
been signed/endorsed is
normally
stored in the smart card. Fig. 2 below
shows the working of an electronic check
in its typical
format:
Fig.
2
A
payer uses the electronic check
book device in his computer
system to generate a blank electronic
check
after
filling the information regarding amount,
date etc., and the electronic
check is digitally signed by
the
payer
through his private key. A
certificate issued by the payer bank authenticating
public key of the payer
is
also
attached with the electronic check. This
information is then sent to the
payee in a secure envelope
through
email. A secure envelop is created
when a user encrypts any
information with a symmetric
key, and
113
E-COMMERCE
IT430
VU
then
that symmetric key itself is
encrypted with the public
key of the receiver. Accordingly, the
payee, in this
case,
decrypts the secure envelop by first
retrieving the symmetric key (by
applying his private key),
and
then
using that symmetric key to
decrypt the information contained in the electronic
check. The payee
endorses
(counter-signs) the check using
some secure hardware device
such as a smart card and
forwards
the
check to the payee's bank in the form of
a secure envelop. The bank clears the
check with the help
of
traditional
Automated Clearing House (ACH).
Accordingly, the account of the payer is
debited and the
payee's
account is credited. The
banks send email statement
to the respective parties.
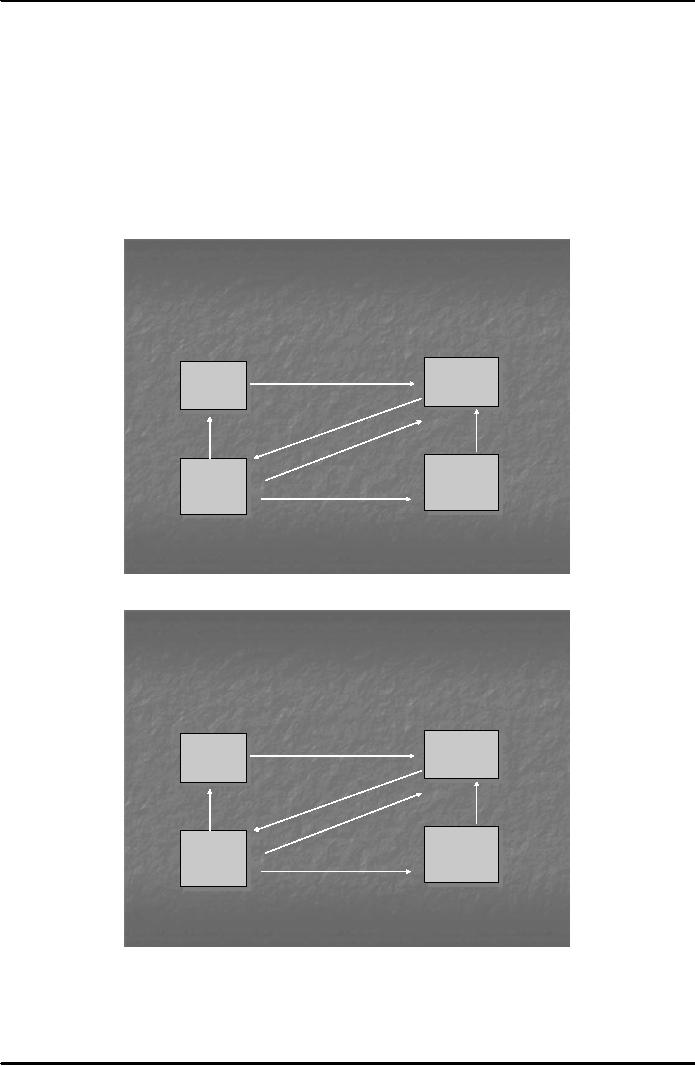
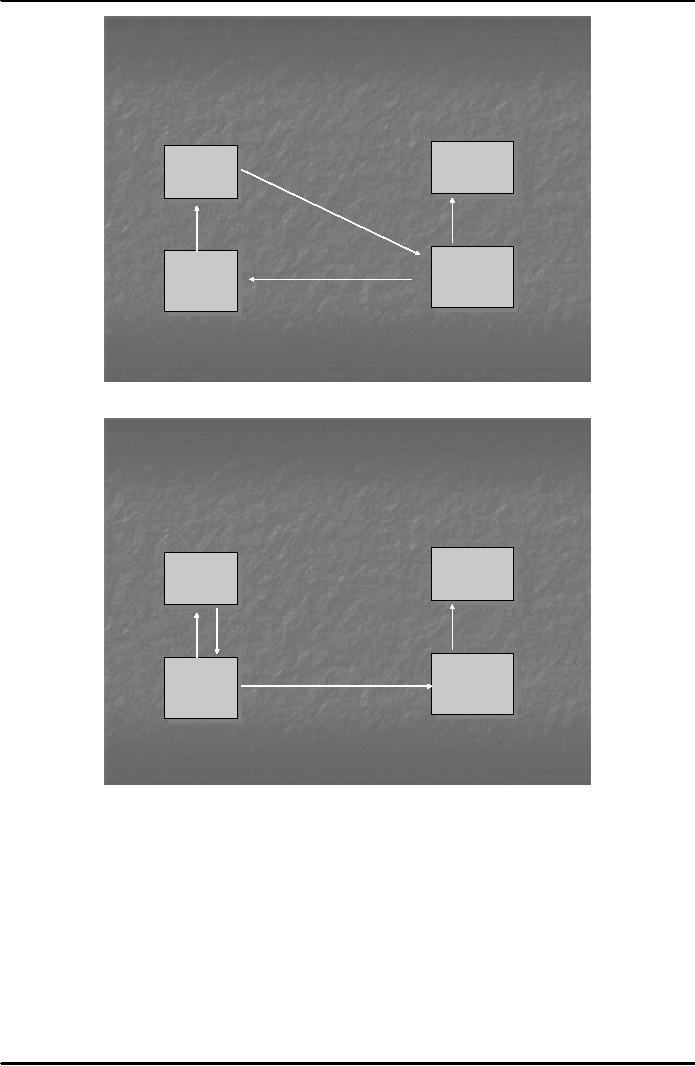
Depending
on the availability of processing infrastructure,
there are four different
scenarios for the
processing
of an electronic check. These
are shown below in figures
3-6. EFT stands for
`electronic
funds
transfer'.
Endorse
Write
1.
Pay
Paayee
P yee
Paayer
P yer
2.Cash
5.
Report
6.
Statement
3.
Notify
Paayeess
P yee'
'
Paayerss
P yer'
'
Baank
B nk
Baank
B nk
4.
EFT
Credit
Debit
Fig.
3
Endorse
Write
1.
Pay
Paayee
P yee
Paayer
P yer
2.Cash
5.
Report
6.
Statement
3.
Notify
Paayeess
P yee'
'
Paayerss
P yer'
'
Baank
B nk
Baank
B nk
4.
EFT
Credit
Debit
Fig.
4
114
E-COMMERCE
IT430
VU
Write
1.
Pay
Paayee
P yee
Paayer
P yer
3.
Accounts
4.
Statement
Receivable
Update
Paayeess
P yee'
'
Paayerss
P yer'
'
Baank
B nk
Baank
B nk
2.
Clear
Endorse &
Credit
Debit
Fig.
5
Write
Paayee
P yee
Paayer
P yer
3.
Accounts
4.
Statement
1.
Pay
Receivable
Update
Paayeess
P yee'
'
Paayerss
P yer'
'
Baank
B nk
Baank
B nk
2.
EFT
Credit
Debit
Fig.
6
115
Table of Contents:
- E-COMMERCE
- WHAT IS A NETWORK
- HOW MANY CLASS A, B, C NETWORKS AND HOSTS ARE POSSIBLE
- NETWORKING DEVICES
- BASICS OF HTML 1
- BASICS OF HTML 2
- TEXT BOXES, CHECK BOXES, RADIO BUTTONS
- FRAMES AND IMAGES IN HTML
- TAG ATTRIBUTES, SOUNDS FILES, ANIMATIONS
- STYLE SHEETS 1
- STYLE SHEETS 2
- SOME USEFUL STYLE SHEETS PROPERTIES
- JAVA SCRIPTING 1
- JAVA SCRIPTING 2
- JAVA SCRIPTING 3
- JAVA SCRIPTING AND XML
- CLIENT AND SERVER SIDE PROCESSING OF DATA
- APPLETS, CGI SCRIPTS
- MAINTAINING STATE IN A STATELESS SYSTEM
- INTEGRATION WITH ERP SYSTEMS
- FIREWALLS
- CRYPTOGRAPHY
- HASH FUNCTION AND MESSAGE DIGEST
- SYMMETRIC KEY ALGORITHMS
- VIRTUAL PIN PAYMENT SYSTEM
- E-CASH PAYMENT SYSTEM 1
- E-CASH PAYMENT SYSTEM 2
- SECURE SOCKET LAYER (SSL)
- E-BUSINESS: DISADVANTAGES OF E-BUSINESS
- E-BUSINESS REVENUE MODELS
- E-MAIL MARKETING
- CUSTOMER RELATIONSHIP MANAGEMENT (CRM)
- META INFORMATION
- DATA MINING
- CONFIDENCE AND SUPPORT
- ELECTRONIC DATA INTERCHANGE (EDI)
- PERSONAL FINANCE ONLINE
- SUPPLY CHAIN
- PORTER’S MODEL OF COMPETITIVE RIVALRY
- BARRIERS TO INTERNATIONAL E-COMMERCE
- ELECTRONIC TRANSACTIONS ORDINANCE, 2002 - 1
- ELECTRONIC TRANSACTIONS ORDINANCE, 2002 - 2
- ELECTRONIC TRANSACTIONS ORDINANCE, 2002 - 3
- GLOBAL LEGAL ISSUES OF E-COMMERCE - 1
- GLOBAL LEGAL ISSUES OF E-COMMERCE - 2