 |
SYMMETRIC KEY ALGORITHMS |
| << HASH FUNCTION AND MESSAGE DIGEST |
| VIRTUAL PIN PAYMENT SYSTEM >> |
E-COMMERCE
IT430
VU
Lesson
24
SYMMETRIC
KEY ALGORITHMS
Cryptographic
algorithms are measured in terms of
key length. Following is the list of
some popular
symmetric
key algorithms:
DES
(Data Encryption Standard) 56
bits
IDEA
(International Data Encryption Algorithm
(IDEA) 128 bits
RC2
(block cipher) 1-2048 bits
RC4
(stream cipher) 1-2048 bits
Rinjdael
128-256 bits
Attacks
on Symmetric Key
Algorithms
Following
attacks have been reported on
symmetric key algorithms:
Key
Search Attacks
Cryptanalysis
System-based
Attacks
Key
Search (Brute Force) Attacks
In this type of
attack an attempt is made by the attacker
to decrypt the message with every
possible key.
Thus,
the greater the key length, the more
difficult it is to identify the
key.
Cryptanalysis
Encryption
algorithms can be defeated by using a
combination of sophisticated mathematics
and computing
power so
that many encrypted messages
can be deciphered without
knowing the key. Such type of an
attack
is
called cryptanalysis.
System-Based
Attacks
In it the
attack is made on the cryptographic
system that uses the cryptographic
algorithm without
actually
attacking the
algorithm itself.
Public
Key Algorithms
Following
is the list some popular
public key algorithms:
DSS
Digital Signature Standard
based on DSA (Digital
Standard Algorithm)
key
length is between 512-1024
bits
RSA
Elliptic
Curves
Attacks
on Public Key
Algorithms
Key
Search Attacks
The
public key and its
corresponding private key are
linked with each other
with the help of a
large
composite
number. These attacks attempt to derive the
private key from its
corresponding public key
using
that
number. According to an estimate 1024
bit RSA public key
may be factored due to fast
computers by
2020.
Note that both symmetric
and asymmetric algorithms are
based on different techniques. In
case of
108
E-COMMERCE
IT430
VU
asymmetric
algorithms the increase in key length
does not much increase the
difficulty level for the
attacker
as
compared to symmetric algorithms. Thus, a
128-bit RC2 symmetric key
may prove to be much
stronger
than a
1024 bit RSA asymmetric
public key.
Analytical
Attacks
Such
attacks use some fundamental
flaw in the mathematical problem on
which the encryption system
itself
is
based so as to break the
encryption.
Quantum
computing is the branch of computer
science that deals with the
development of cryptographic
algorithms. It
can also be used to find
flaws in the cryptographic system/algorithms and to
launch attacks.
Electronic
Payment Systems
Most
of the electronic payment systems on
internet use cryptography in one
way or the other to
ensure
confidentiality
and security of the payment
information. Some of the popular
payment systems on
internet
include the
credit-card based payment
systems, electronic checks, electronic
cash, micro-payment systems
(milicent, payword
etc.)
The
Process of Using Credit
Cards
It may
be useful to see how payment is
made through a credit card in the
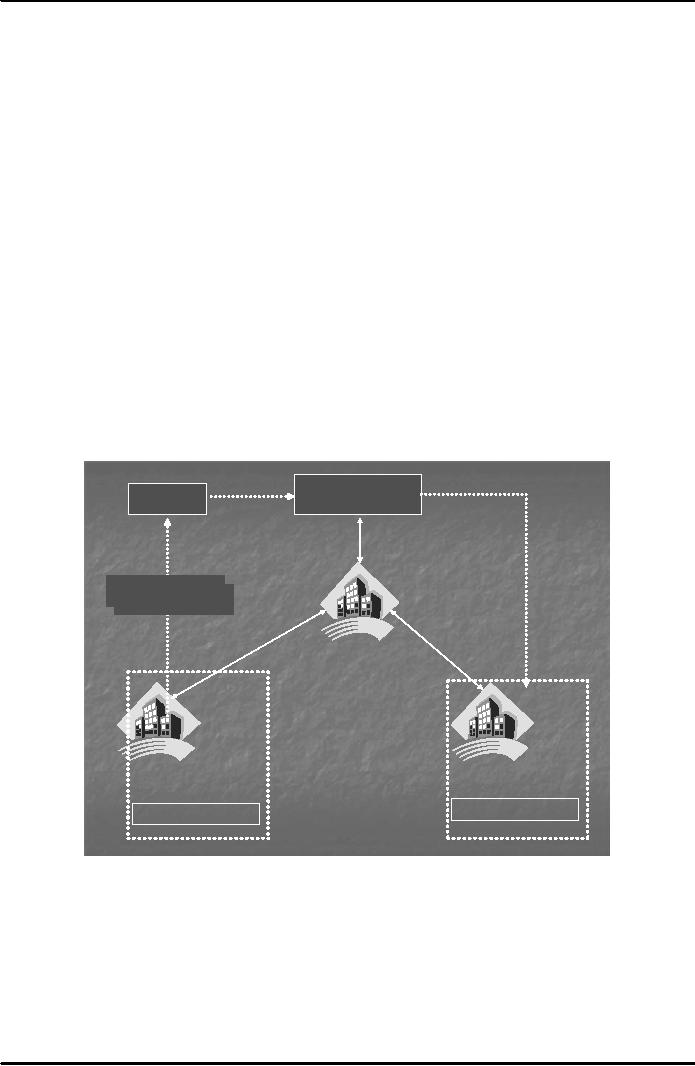
traditional sense. Fig. 1
below
shows
the steps to be followed in this
regard:
Merchant
Card
Holder
2.
Show
Credit
Card
3.
Authorization
4.
Capture
1.Issue
Credit Card
1.Issue
Credit Card
5.
r
Pa
fe
ns
y
m
a
Tr
en
nt
t
ou
Re
Am
qu
Card
Brand
6.
es
t
Acquirer
Bank
Issuer
Bank
Merchant
Account
Cardholder
Account
Fig.
1
1. A
potential cardholder requests an issuing
bank in which the cardholder may have an
account,
the
issuance of a card brand (like
Visa or MasterCard). The
issuing bank approves (or
denies)
the application. If
approved, a plastic card is physically
delivered to the customer's address
by
mail.
The card is activated as
soon as the cardholder calls the bank for
initiation and signs
the
back
of the card.
2. The
cardholder shows the card to a merchant
whenever he or she needs to
pay for a product or
service.
3. The
merchant then asks for
approval from the brand company (Visa
etc.) and the transaction
is
paid by credit.
The merchant keeps a sales
slip.
109
E-COMMERCE
IT430
VU
4. The
merchant sends the slip to the acquirer
bank and pays a fee for the
service. This is called
a
capturing
process.
5. The
acquirer bank requests the brand to clear
for the credit amount and gets
paid.
6.
Then the brand asks for
clearance to the issuer bank. The amount
is transferred from issuer
to
brand.
The same amount is deducted
from the cardholder's account in the
issuing bank.
Note
that in case of a credit card the
issuer bank charges interest
from the client at a specified
rate on the
amount
lent. On the other hand, in
case of a debit card no such
interest is payable since the
customer uses
his/her
own money in that
case.
Virtual
PIN Payment System
It is
one of the earliest credit card-based
systems launched for the
internet in 1994 by a company;
First
Virtual
Holdings, Inc. Virtual PIN
system does not involve the
use of encryption. Payment is made
through
the credit
card in this system. The objective
was to allow the selling of low-value
information items
without
the
use of any special client
software or hardware.
Both
merchants and buyers are
required to register with First Virtual
(FV). A buyer registering with
FV
forwards
his or her credit card
details and email address to
FV and in exchange receives a
pass phrase called,
Virtual
PIN. Buyer makes a telephone
call to FV to provide his/her credit
card number. FV establishes a
link
between the Virtual PIN and the credit
card number without using the credit
card number on the
network.
A Merchant goes through a
similar registration process. He provides
his bank details to FV and
is
given a
merchant Virtual PIN. The
merchant can now request to
process payments from
registered FV
customers.
The transfer takes place
with the help of Automated
Clearing House (ACH) service.
Note that
an ACH
is a centralized system to which
different banks are electronically
connected forming a network
for
clearing
payment requests. At the end the
payment proceeds from the credit
card issuer bank to the
account
of the
merchant with acquirer bank
(merchant's bank) through ACH, after FV
deducts a per-transaction
charge
for its services.
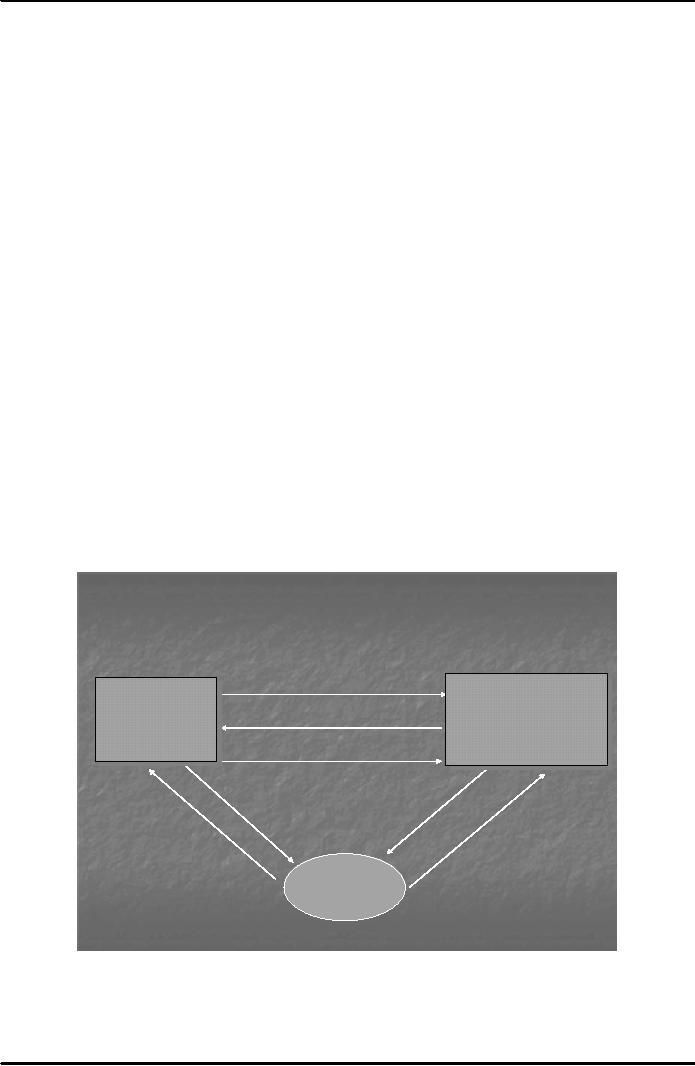
Fig. 2
below shows the working of
Virtual PIN payment
system.
Buying with First
Virtual
2. Account ID
Valid?
FirrstVirrtualIInternet
Fist Vitual
nternet
PaymenttSysstem
Paymen Sy
tem
Web
Serrver
Web
Sever
3. Account
OK!
Serrver
Sever
((Sellilng
Sel
ing
Goodss)
Good
)
5. Transaction
Details
4.
Information
Goods
6.
Satisfied?
1. Account
ID
7.
Accept/Reject or
Fraud
Indication
Buyer
Fig.
2
A buyer
browses the web server where
FV registered merchant is selling
goods. The buyer is asked to
enter
his/her
Virtual PIN by the merchant site
(step
1). Merchant
queries the FV Internet Payment
System
Server
(FVIPSS) to confirm Virtual PIN (step
2). If
Virtual PIN is not blacklisted (step
3), the
merchant
110

E-COMMERCE
IT430
VU
may
acknowledge this fact to the buyer by email
and sends the goods, and
also sends transaction
details to
FV (steps
4 & 5). FVIPSS or simply
FV server sends email to the buyer if the
goods were
satisfactory
(step
6). There
are three possible answers
to that (step
7). If the
answer is "accept" then the
payment
proceeds,
in case the answer is "reject" it
means that either the goods
have not been received or
the buyer is
not
satisfied with the quality of
goods. Then the payment is
not made to the merchant. If the
answer
indicates
"fraud" it means that the
goods were never ordered. In
such an eventuality the FVIPSS
immediately
blacklists Virtual PIN so that it cannot
be used in the future.
Time
period may be a few minutes to a
few days for answering the
email in step no. 6 above,
otherwise
FV
shall proceed to arrange the
payment. If a Virtual PIN has
been stolen and the buyer
does not
indicate
fraud within the time period
for answering the said email
the bogus transactions are
possible
before the
Pin is finally blacklisted. A
stolen credit card number can
also be used to set up
Virtual PIN
associated
with an email address
controlled by the attacker to carry
out bogus
transactions.
111
Table of Contents:
- E-COMMERCE
- WHAT IS A NETWORK
- HOW MANY CLASS A, B, C NETWORKS AND HOSTS ARE POSSIBLE
- NETWORKING DEVICES
- BASICS OF HTML 1
- BASICS OF HTML 2
- TEXT BOXES, CHECK BOXES, RADIO BUTTONS
- FRAMES AND IMAGES IN HTML
- TAG ATTRIBUTES, SOUNDS FILES, ANIMATIONS
- STYLE SHEETS 1
- STYLE SHEETS 2
- SOME USEFUL STYLE SHEETS PROPERTIES
- JAVA SCRIPTING 1
- JAVA SCRIPTING 2
- JAVA SCRIPTING 3
- JAVA SCRIPTING AND XML
- CLIENT AND SERVER SIDE PROCESSING OF DATA
- APPLETS, CGI SCRIPTS
- MAINTAINING STATE IN A STATELESS SYSTEM
- INTEGRATION WITH ERP SYSTEMS
- FIREWALLS
- CRYPTOGRAPHY
- HASH FUNCTION AND MESSAGE DIGEST
- SYMMETRIC KEY ALGORITHMS
- VIRTUAL PIN PAYMENT SYSTEM
- E-CASH PAYMENT SYSTEM 1
- E-CASH PAYMENT SYSTEM 2
- SECURE SOCKET LAYER (SSL)
- E-BUSINESS: DISADVANTAGES OF E-BUSINESS
- E-BUSINESS REVENUE MODELS
- E-MAIL MARKETING
- CUSTOMER RELATIONSHIP MANAGEMENT (CRM)
- META INFORMATION
- DATA MINING
- CONFIDENCE AND SUPPORT
- ELECTRONIC DATA INTERCHANGE (EDI)
- PERSONAL FINANCE ONLINE
- SUPPLY CHAIN
- PORTER’S MODEL OF COMPETITIVE RIVALRY
- BARRIERS TO INTERNATIONAL E-COMMERCE
- ELECTRONIC TRANSACTIONS ORDINANCE, 2002 - 1
- ELECTRONIC TRANSACTIONS ORDINANCE, 2002 - 2
- ELECTRONIC TRANSACTIONS ORDINANCE, 2002 - 3
- GLOBAL LEGAL ISSUES OF E-COMMERCE - 1
- GLOBAL LEGAL ISSUES OF E-COMMERCE - 2