 |
FIREWALLS |
| << INTEGRATION WITH ERP SYSTEMS |
| CRYPTOGRAPHY >> |
E-COMMERCE
IT430
VU
Lesson
21
FIREWALLS
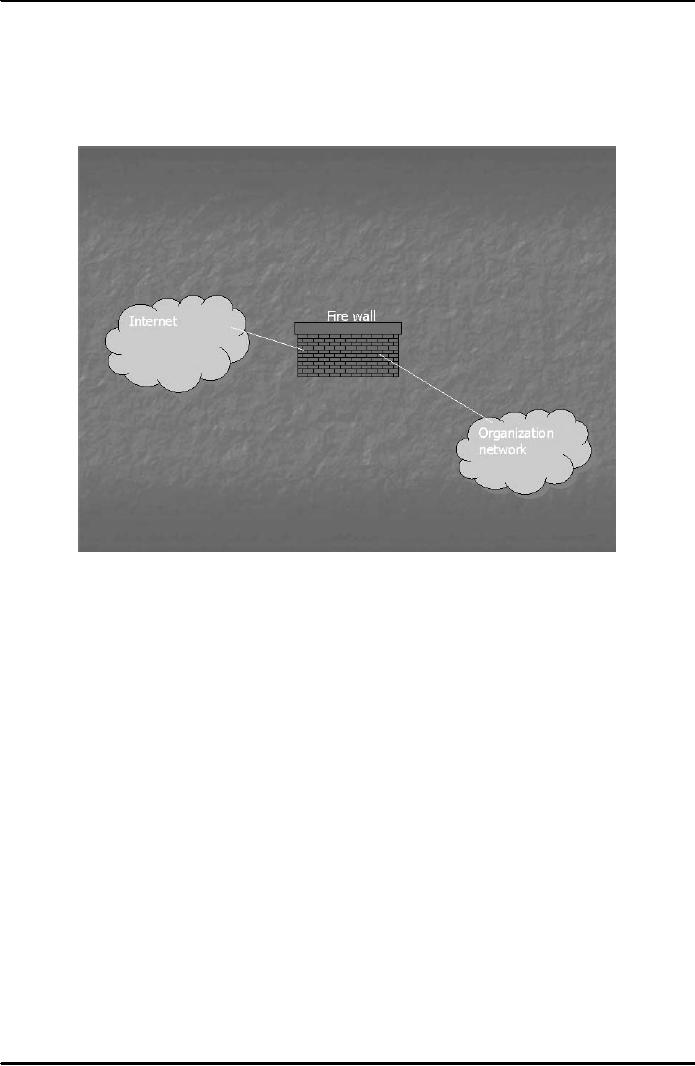
A
firewall is a combination of hardware
and software that sits
between the internet and
internal network of
an organization to
protect the network from
outside attack (Fig. 1). It
can examine the data entering
or
leaving
from the network and can
filter the data according to
certain rules, thus,
protects the network
from
an
attack. There are three main
types of firewalls detailed as
follows:
Fig.
1
Packet
filter firewall
It
uses a set of rules to
determine whether outgoing or incoming
data packets are allowed to
pass through
the
firewall. For example, we
can, as a rule, specify IP addresses of
sending devices such that
packets from
these
IP addresses are not allowed to
enter the network. The Firewall
would stop them from entering.
A
packet
filter firewall is the simplest type of
firewalls which operates at data
link and network layers of
the
OSI
model.
Circuit
level firewall
It is
quite similar to the packet
filter firewall. It also works on the
basis of a set of rules for
filtering packets
but
operates at the transport layer of the
OSI Model so has greater
functionality. As a rule, the higher the
layer
of OSI model where a firewall
operates, the more sophisticated is the
firewall. It can make
packets sent
from
internal network to a destination outside
the firewall appear as if they originated at the
firewall. Thus
information
regarding hosts on the internal
network remains secret. It
can also determine whether
TCP/IP
connection
between a host and a machine
outside firewall has been
properly established. Thus it
can cut off
any
connection which has been hijacked by a
hacker trying to pass
through the firewall.
Application
gateway firewall
It
operates at application layer of the
OSI Model. It uses strong
user authentication to verify identity of
a
host
attempting to connect to the network
using application layer protocols
such us FTP. In contrast to
packet
filter firewall, it filters the
requests rather than packets
entering/leaving the network. It can
block any
outgoing
HTTP or FTP requests. It can
prevent employees of a company
inside a firewall
from
downloading
potentially dangerous programs
from the outside. In other
words, this type of firewall is
used
96
E-COMMERCE
IT430
VU
to
control connections thus
employees of a company can be
restricted from connecting to certain
web sites.
We can
combine circuit level capabilities with
application gateway services to
form Hybrid type of a
firewall.
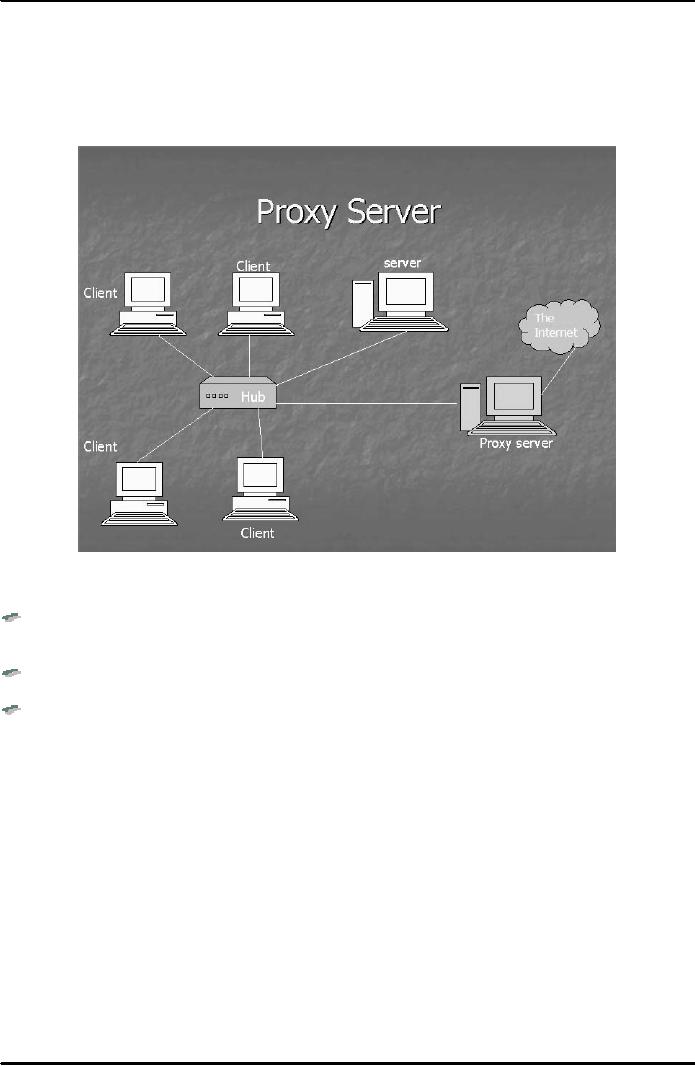
Proxy
server
A
proxy server sits between an
internal trusted network and
the untrusted network, that is,
internet, as
you
can
see in Fig. 2 below.
Fig.
2
Mainly,
it can do three things:
An
http request from the
browser goes to proxy
server. It can affix its
own IP address instead of
IP
address
of the requesting machine; thus, it
hides the information of the host. It
downloads the
requested
page itself and afterwards
supplies it to the user.
It can
also act as a firewall
filtering requests for
certain web pages.
An
important job it can do is to
speed up the processing of http
requests by caching web
pages.
Caching
means that it can store the
requested web pages in its
memory (cache memory) for a
certain
period.
The advantage of caching is
that for subsequent web
page requests the time of supply of
the
web
pages is reduced. Instead of sending the
request to actual web
server, the proxy server can
quickly
supply the
web page stored in its
cache memory, thus, it saves
the time of downloading the page.
Virtual
private network (VPN)
Suppose
that a client is sitting at a local
branch network of a company
and wants to become part of
a
bigger,
head office network of that
company located far away.
One option for him is to set
up a dial up
connection,
which means that he can be
connected to a server machine
lying in the head office
network
through
a direct telephone line. That server
machine may be called a Remote
Access Server (RAS) and
the
client may be called a Remote
Access Client (RAC). Remote
access is a two way process
so both RAS
and
RAC must be configured, first.
Some windows operating systems provide
the facility to configure the
RAS
and RAC. Basically, the
client specifies the phone
no. of RAS while
configuring. After both RAS
and
RAC
are configured, the client enters
identification information (password
etc.) and clicks at
"Dial".
Accordingly,
phone no. of RAS is dialed
and connection with RAS is
setup. Once clients are
connected to
RAS,
they can access the remote
company network and its
resources servers, printers etc. A
protocol,
97
E-COMMERCE
IT430
VU
Point
to Point Protocol (PPP), is
used to set up the dial up connection
between RAC and RAS
for exchange
of
data packets.
A VPN
provides another option of remote access.
It is defined as a secure, dedicated
point to point
connection
over the internet. In VPN we use
internet infrastructure for connection
instead of a special
telephone
line. Both RAS (also
called tunnel server) and
RAC (also called tunnel
client) are connected to
the
internet.
Initially, both are configured
for VPN. IP address of
tunnel server must be
specified during the
configuration
of tunnel client (instead of
phone no.). The option of VPN is
available if we explore the menu
`Internet
Options'. We can enable VPN,
thus. Similarly, tunnel server should
also be configured so that a
client's
request for access can be
authenticated. VPN connections or
tunnels are managed by Point
to Point
Tunneling
Protocol (PPTP) which due to
encryption provides secure transport of
private communications
over
the public internet. A VPN connection
thus can be created between
the branch office and
the
corporate
head office.
VPN is
a cost saving measure as
compared to simple remote
access using dial up connection. In
VPN one
makes
a local call to the ISP and
then using ISP's infrastructure,
routers etc. one is
connected to the
internet.
In other words a client can
become part of the remote
network through the internet.
Note that a
tunnel
client just incurs the cost of a
local call to the ISP and
yet he can remain part of
the remote corporate
network
for many hours. On the other
hand, in case of dial up connection
for remote access one
has to pay
the
cost of a long distance call
for as many no. of hours as
one wants to be connected to the
remote
corporate
network. This is going to be very expensive.
VPN is the example of an extranet.
You know that
when
two or more intranets are
connected to each other they
form an extranet. A manufacturing
company
thus
can be connected to its
suppliers of raw material
and its distributors through
VPN.
Security
the biggest
challenge
There is a
consensus that the issue of computer
and data security is the
biggest hurdle in the growth of
e-
commerce.
Web servers also face this
security threat. Programs that
run on a server have the
potential to
damage
databases, abnormally terminate server
software or make changes in the
information placed there.
A
number of
international organizations have
been formed to share
information and combat
security threats
to
computers and computer networks. The
names of two such
organizations are
worth-mentioning:
Computer
Emergency Response Team
(CERT)
Systems
Administrator, Audit, Network
and Security Institute (SANS
Institute)
The
best response that the
experts have come up with to
tackle the security issue is in
terms of
cryptography.
Cryptography
Cryptography is the
technique of converting a message into
unintelligible or non-understandable form
such
that
even if some unauthorized or unwanted
person intercepts the message
he/she would still not be
able to
make
any sense out of it.
Cryptography is thousands of years
old.
Techniques
used for cryptography Substitution In
substitution we replace each
letter in the message
with
another to
make the message non-understandable.
For example, each letter
"a" in the message can
be
replaced
with letter "d" and letter
"b" with letter "e" and so
on. Transposition It is based on
scrambling the
characters
in a message. A transposition system may
first write a message into a
table row by row then
the
message
can be read and rewritten
column by column to make it scrambled (see
Fig. 3).
98

E-COMMERCE
IT430
VU
Fig.
3
Historically,
cryptography has long been
used as a military technology. Julis
Ceaser used a simple
transposition
cipher to scramble messages to give instructions to
his commanders in the
battlefield.
Similarly,
Hitler used Enigma encryption cipher to
scramble messages sent by
radio to German armies
and
u-boats
during the Second World War.
Cryptography has also been
used for non-military
purposes over the
centuries.
There are records of people using
cryptography to protect religious secrets
and to hide secrets of
science
and industry. In recent years, the
use of cryptography in business and
commerce appears to
have
surpassed
its earlier use. It has
made the rapid commercialization of
internet possible.
Without
cryptography, it is
doubtful that banks,
businesses and individuals
would feel safe doing
business online.
99
Table of Contents:
- E-COMMERCE
- WHAT IS A NETWORK
- HOW MANY CLASS A, B, C NETWORKS AND HOSTS ARE POSSIBLE
- NETWORKING DEVICES
- BASICS OF HTML 1
- BASICS OF HTML 2
- TEXT BOXES, CHECK BOXES, RADIO BUTTONS
- FRAMES AND IMAGES IN HTML
- TAG ATTRIBUTES, SOUNDS FILES, ANIMATIONS
- STYLE SHEETS 1
- STYLE SHEETS 2
- SOME USEFUL STYLE SHEETS PROPERTIES
- JAVA SCRIPTING 1
- JAVA SCRIPTING 2
- JAVA SCRIPTING 3
- JAVA SCRIPTING AND XML
- CLIENT AND SERVER SIDE PROCESSING OF DATA
- APPLETS, CGI SCRIPTS
- MAINTAINING STATE IN A STATELESS SYSTEM
- INTEGRATION WITH ERP SYSTEMS
- FIREWALLS
- CRYPTOGRAPHY
- HASH FUNCTION AND MESSAGE DIGEST
- SYMMETRIC KEY ALGORITHMS
- VIRTUAL PIN PAYMENT SYSTEM
- E-CASH PAYMENT SYSTEM 1
- E-CASH PAYMENT SYSTEM 2
- SECURE SOCKET LAYER (SSL)
- E-BUSINESS: DISADVANTAGES OF E-BUSINESS
- E-BUSINESS REVENUE MODELS
- E-MAIL MARKETING
- CUSTOMER RELATIONSHIP MANAGEMENT (CRM)
- META INFORMATION
- DATA MINING
- CONFIDENCE AND SUPPORT
- ELECTRONIC DATA INTERCHANGE (EDI)
- PERSONAL FINANCE ONLINE
- SUPPLY CHAIN
- PORTER’S MODEL OF COMPETITIVE RIVALRY
- BARRIERS TO INTERNATIONAL E-COMMERCE
- ELECTRONIC TRANSACTIONS ORDINANCE, 2002 - 1
- ELECTRONIC TRANSACTIONS ORDINANCE, 2002 - 2
- ELECTRONIC TRANSACTIONS ORDINANCE, 2002 - 3
- GLOBAL LEGAL ISSUES OF E-COMMERCE - 1
- GLOBAL LEGAL ISSUES OF E-COMMERCE - 2